It’s been a fairly interesting week overall in storage.
There’s still been a lot of chatter about FAST, EMC’s new system for having LUNs automatically moved between different tiers of storage. I clearly need to read up more about FAST, because so far I don’t see it so much as FAST but as 2nd gear. Sure, being able to automatically move whole LUNs around is nice, but I thought the magic was in sub-LUN migration years ago when I saw a Compellent demo on it. Clearly I’m missing something, because a lot of people have been getting very excited. Then again, my focus in storage has been protecting it rather than optimising primary access, so it’s likely I’ll get more interested in it as I read more about it.
Over at Search Storage, there was an interesting article about data reduction vs data deduplication and compression. This prompted me to pull my finger out, and so sometime soon I’ll have another blog article myself here called All this Deduplication is Making me Thirsty. I’ll leave it as an exercise to the reader what I’m talking about (or a surprise for the article.)
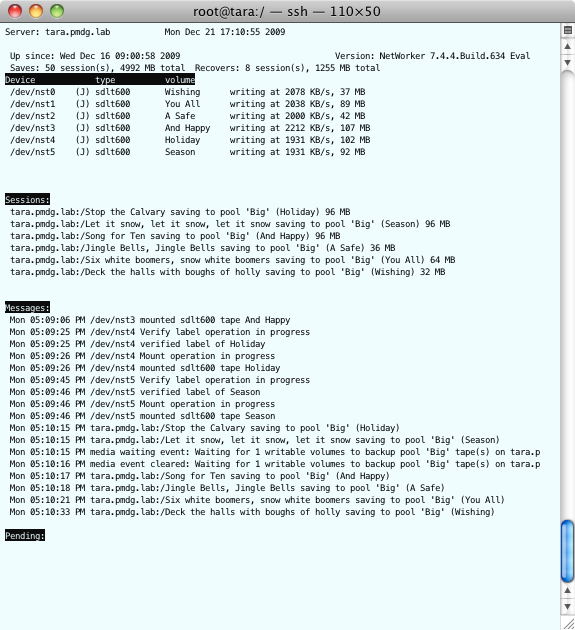
Moving on, I found this excellent article by Drew Robb over at ServerWatch called Tape vs Disk: Tape Refuses to be Evicted. Regular readers of my blog will know that my opinion on the “tape is dead” pronouncements we get every few months is to blow a big fat raspberry at move on. Drew’s article was pointedly useful, in that he dug into the IDC studies on tape sales. While a lot of the media is enjoying running around saying that IDC shows that tape sales are declining, they’re not telling the whole truth, as Drew points out. In actual fact, it’s the low end tape sales that are falling off quite a bit, but the enterprise stuff is still running along quite nicely. This is completely understandable – I’ve seen a lot of small businesses that used to rely on cheap and cheerful tapes like DAT transition to more reliable and longer lasting media, but I don’t see a lot of enterprises killing tape. (What’s the old saying from that old ad – linear serpentine, good for data; helical scan, good for parties … I think the party is fizzing out, but the data is still going strong…)
I think when it comes to handing out awards (if I were to do that) for the coolest storage blog entries this week, they have to go to Storagebod, with his 7 part series of letters to father christmas – including the final one asking for presents for other bloggers.
Over at Grumpy Storage, Ian penned a fantastic article called Show me the Money. I think this should be mandatory reading for every sales person and consultant in the tech industry – certainly in previous companies I’ve dealt with sales people who have been shot down and lost deals for failing to follow these rules that should be self evident.
On the lighter side, someone (apologies, I can’t remember who) twittered a link to Death By Powerpoint. This should be mandatory watching for everyone in business, full stop.
On a more local front, Brian over at Going Virtual has just done his wish list for updates to NetWorker for 2010 in relation to virtualisation support.
On a slightly different note, our Australian government has decided it’s going to attempt to introduce national mandatory net censorship laws next year. I would say what I think about such draconian subjects except it would undoubtedly be retroactively censored next year and this article deleted. I’d hate to upset my article count, so suffice to say, in a more polite way, that I hope they take notice of online polls that show upwards of 95% of people against the idea.
Over at Daring Fireball (yes, I know, not a storage blog), John Gruber has a rather excellent analysis of the garbage that’s been coming out of AT&T lately. Apparently they only want customers to buy, not use bandwidth. Silly, selfish users who expect to be able to buy and then use their services are apparently to blame for profit obsessed companies that have no interest in upgrading their infrastructure to meet needs.
Over on the The Register, there was a story about Stratus putting their money where their mouths are. Good on you Stratus.
Next to last, as a bit of self-advertising, I took time out from this blog to write up some thoughts on all those marketing slides that encourage people to do TCO calculations to compare pushing infrastructure out of the data centre and into the Public Cloud, and suggested that an alternate calculation needs to follow, one that I call Total Cost of Impact.
One final comment: please go and see Avatar. If you don’t, you’ll be missing out on the greatest block buster of all time (so far). If you’re a Star Wars fan, you doubly need to see it, so you can understand what a good movie looks like.